Frequently Asked Questions
All You Ever Wanted to Know About Insurance
Risk Management: Safety
Cyber Security
Wire Transfer Fraud Quadruped in 2017 – Beazley

Cyber-criminals are using ever-more sophisticated methods to exploit human weaknesses in an organization's cyber defenses, reports Beaszley Group, a worldwide specialty insurer. Under fraudulent instruction scams, criminals use hacking and phishing techniques to accumulate information that allows them to send plausible-looking requests to transfer funds to bogus accounts. In addition to losing money, organizations may also have to conduct exhaustive systems analysis to ensure that individuals' personal and private data has not been compromised.
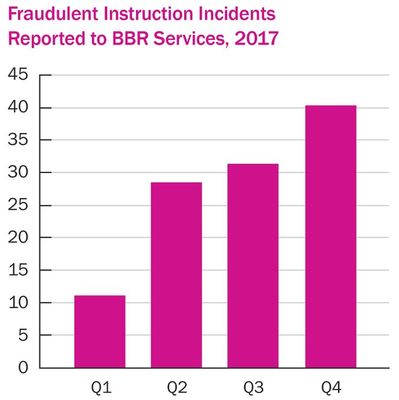
CLAIMS QUADRUPLED IN 2017
Claims data recorded by Beazley indicates that organizations are facing an increased threat to their operations from fraudulent instruction scams. Fraudulent instruction incidents reported to Beazley Breach Response Services (BBR Services) quadrupled in 2017, with policy holders incurring losses ranging from a few thousand dollars upto $3 million. With claims amounts in 2017 averaging $352,000, fraudulent instruction has rapidly become a significant financial threat to many organizations.
UNINSURED CLAIMS
Fraudulent Instruction fraud claims are not usually insured. The typical Commercial Insurance policy contains exclusions in the Property, Crime and Employee Dishonesty sections that prevent recovery of this type of claim. Special coverage is required and is just now becoming readily available as a covered section to Cyber Insurance policies.
HOW FRAUDULENT INSTRUCTION WORKS

After a successful phishing expedition or through the installation of a key-logger, a criminal can gain insight into company financial protocols related to wire transfers. The criminal then uses a relationship that they have discovered through their phishing activities to provide fake payment instructions, usually by email. The purported source of the payment instructions is often a trusted business partner. Even with no access to earlier communications between the sender and recipient, a "spoofed" email can be created by checking social media for connections, roles or other supporting details.
One such attack came to light when a retail store received complaints from customers about non-delivery of goods for which they had paid by wire transfer. For the retailer however, there was no record of payment. It transpired that the customers had received new wire instructions from the criminals posing as the retailer.
Real estate transactions are frequent targets with the cyber-criminal exploiting the short timeframe for payment to take place. In a recent incident, the cyber criminal compromised a broker's email and sent revised wire transfer instructions, diverting the final payments.
Manufacturers are also vulnerable. In an incident reported to BBR Services, the email account of an employee in the accounting department of a manufacturer was compromised through phishing and the criminal emailed new wire payment instructions to some of the company's customers. Only after customers appeared to have missed payment did the manufacturer discover the account had been compromised.
IF YOU WIRE TRANSFER MONEY, BE VERY CAREFUL
To guard against fraud, you must have a known contact from the company you are paying by wire transfer and follow these steps.
- Telephone Confirmation: Before a wire transfer you must talk with that known contact by phone (at a phone number you know is correct for that business) and confirm the destination bank account routing and bank account numbers. DO NOT DO THIS BY EMAIL.
- Transfer Test: First, wire transfer the smallest payment amount allowed and then call your contact to confirm that funds have arrived.
- Final Transfer: If confirmed, then wire transfer the full payment. Again, confirm receipt by phone to your known contact.
Source: Beazley Breach Insights – January 2018


